Custom Policy Agent
Policies written conversationally, enforced automatically, and dynamic with your codebase.
.webp)
Executive Summary
The DryRun Security Custom Policy Agent brings security policy creation, enforcement, and developer education directly into every pull request (PR) and your repositories. No manual rule writing required.
Unlike static rule engines or cleanup AI tools, the DryRun Security policy engine combines natural language code policies, agentic reasoning in our Custom Policy Agent, and contextual understanding to evaluate code behavior. The result is a code policy engine that is easy-to-use, doubles accuracy, and gives developer-friendly feedback in seconds.
How it works:
- Provide your policy or describe your goal in the Policy Assistant, or start from the Policy Library.
- The Custom Policy Agent interprets the policy and runs it on every pull request, regardless of language or framework.
- Developers receive inline, actionable feedback when enforcement triggers; security teams see how the policy was enforced and why.
Why it’s different:
- Write policies in plain language; no regex or Domain-Specific Language (DSL)
- No rules to maintain across languages or frameworks
- Policies run automatically on every PR
- Built-in developer guidance ensures context and learning at the source
- Agentic orchestration beyond the PR with real-time access to code, context, and risk intelligence
.webp)
Custom Policy Agent: 6 Features for Powerful Policies
DryRun Security goes beyond traditional approaches by combining these powerful tools with the core Custom Policy Agent, creating the most comprehensive and easy-to-use policy engine in application security (AppSec). This integrated solution streamlines policy enforcement and provides unparalleled control over your application security posture.
Explore the six core technologies that fuel our policy engine, and discover how they work in concert to reduce risk and elevate your code security.
1. Natural Language Code Policy Creation
Natural Language Code Policies make it easy to describe what you want to enforce:
- “Do any libraries introduced in this PR violate our internal licensing requirements?”
- “Does this change introduce username enumeration?”
- “Does this code introduce a new API endpoint without authorization enforcement?”
Natural language policies can be written with the Policy Assistant, on their own, or from the library in the Policy Builder.
The engine handles interpretation, context gathering, and enforcement automatically across any tech stack.
No DSL and no rewrites are needed because the policies are model-driven. They adapt to new languages and frameworks automatically. No rule maintenance, no pattern matching, and no brittle syntax.
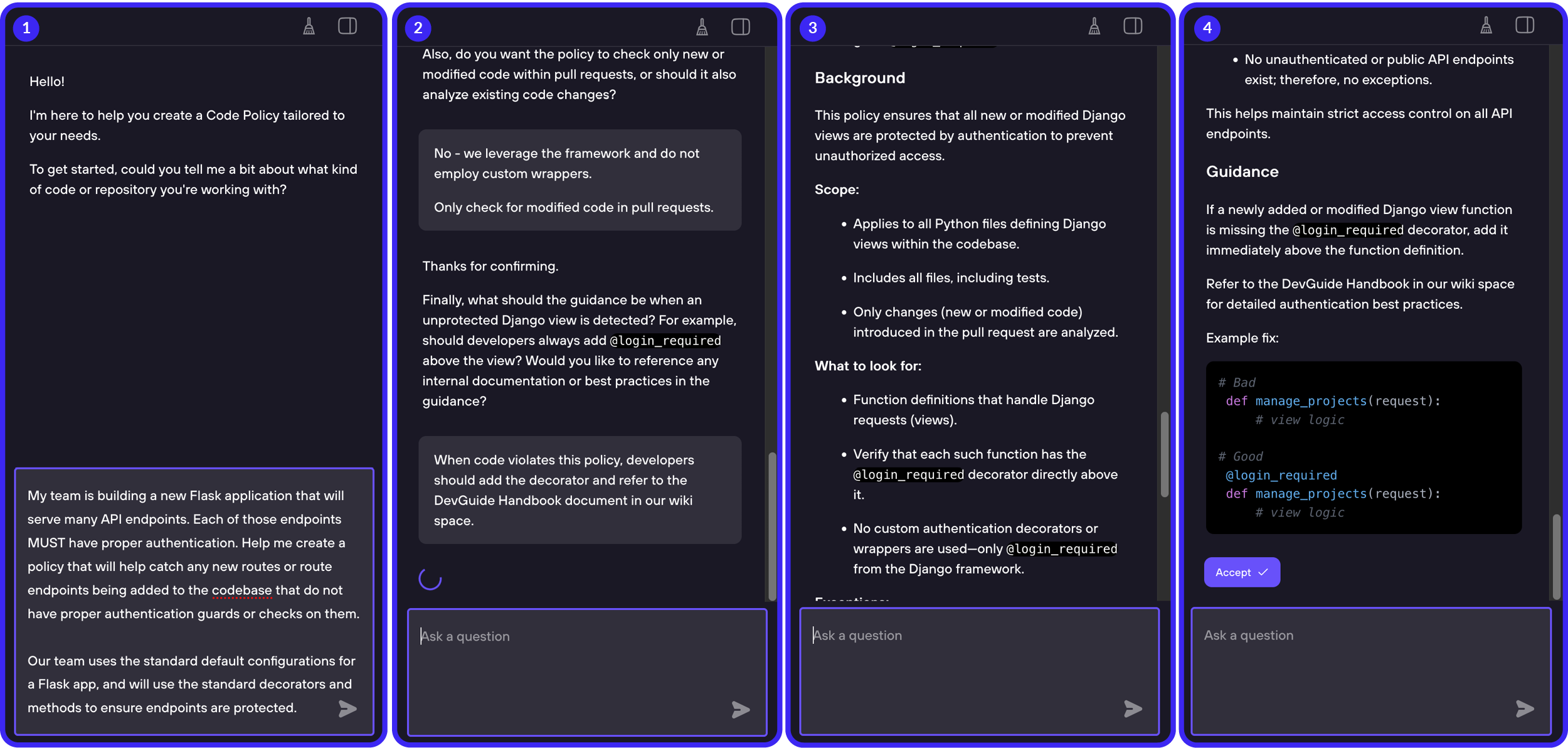
2. Policy Assistant: Guided Policy Creation
Where other platforms offer an “AI cleanup” button, our AI Policy Assistant builds the policy with you from the start.
You describe your goal, and the assistant:
- Asks clarifying, context-specific questions
- Builds a complete, testable policy
- Suggests developer-facing feedback you can include in pull requests
- Provides options for custom remediation and contextual education
Instead of rewriting imperfect policies, you get a correctly structured, high-quality policy on the first try.
Sample sequence of interactive policy creation:
.png)
Now that we have a policy we move to the heart of the DryRun Security policy engine, the Custom Policy Agent.
3. Custom Policy Agent: Policy Enforcement, Everywhere
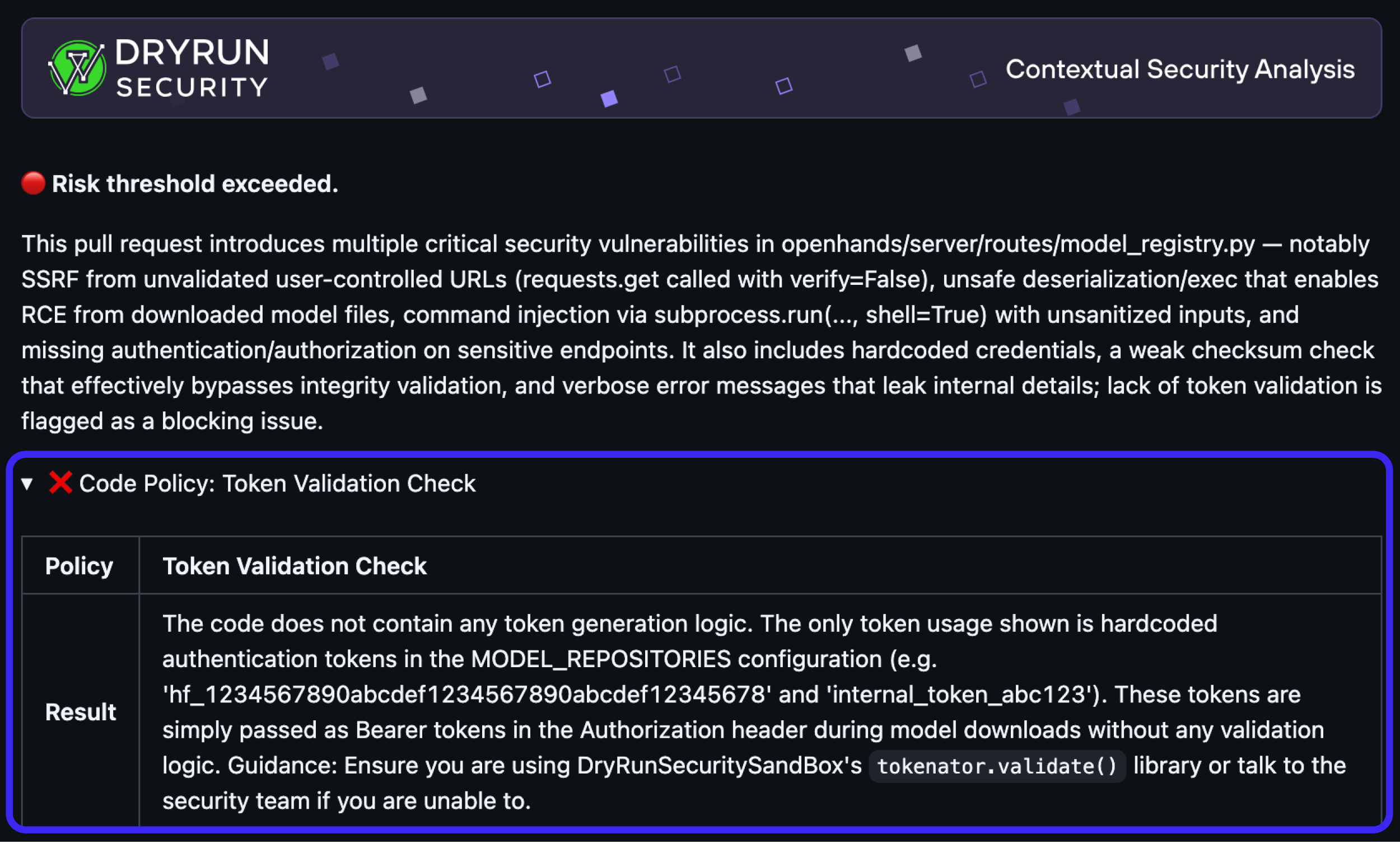
Once a policy is created, the Custom Policy Agent runs it on every pull request, spins up specialized sub-agents as needed, generates an AppSec summary for each finding, and provides inline developer guidance. It is like having an expert AppSec engineer in every pull request across your codebase, providing developer feedback in time with your code.
This moves security from static documentation into active enforcement directly in the CI/CD pipeline.
Example code:
.png)
Caught by this policy:
.png)
Surfaced in the PR:
.png)
And presented in the dashboard:
.png)
Custom Policy Agent controls a network of specialized sub-agents that collaborate to analyze, research, and interpret code. Some of these agents include:
{{table}}
Each agent acts autonomously within its domain, together forming an adaptive intelligence layer that scales across organizations and technology stacks. The Custom Policy Agent takes your policies beyond simple AI overlays common in the industry, working for you to enforce your unique security and compliance requirements on every PR.
4. Developer Guidance: Built-In
Every finding includes developer-facing feedback and not just a failing check. This feedback helps developers understand why a policy triggered and how to fix it, reducing friction between AppSec and engineering. Teams can customize this guidance to fit their tone and workflow, aligning security education with real development activity.
5. The Policy Library: Start Fast, Customize Freely
The Policy Library provides a collection of pre-written, high-value policies that teams can use as-is or adapt in seconds. It’s built to help you start strong and customize quickly.
Users can browse popular policies for common security needs such as secrets detection, authentication changes, or dependency risks. They can then edit the natural-language policy text to match their specific environment. Policies can be instantly tested and tuned in the Policy Builder before enforcement is enabled.
6. The Policy Builder: Test, Tune, and Trust
The Policy Builder lets users test and validate policies against real pull requests before enabling enforcement. It is designed for experimentation, transparency, and confidence. The system allows you to run policies against specific PRs or branches, view accuracy, repeatability, and runtime performance, and iterate and fine-tune policies with immediate feedback.
.png)
.webp)
Summary
The DryRun Security Custom Policy Agent revolutionizes how security teams define, enforce, and communicate security requirements. It replaces fragile, syntax-based rules with dynamic, language-agnostic intelligence that comprehends code behavior and context. It guides developers precisely when needed and continuously adapts to your codebase and technology stack.
The Difference at a Glance
{{table2}}
The Custom Policy Agent combines the flexibility of natural language with the precision of specialized AI agents, making it possible to detect complex, behavior-driven vulnerabilities across any tech stack.
Security should not live in PDFs or meeting notes. With DryRun Security, it lives where it matters most: in your pull requests.
About DryRun Security
DryRun Security created Contextual Security Analysis to detect vulnerabilities ranging from OWASP Top 10 to application-specific logic flaws—all with minimal configuration. Founded by developers who saw the need for practical security, DryRun integrates seamlessly into modern CI/CD pipelines, providing clear, actionable insights that don’t bog down teams.
Want to see more for yourself?
We would love to show you how you can have better coverage and fewer false positives. Reach out to DryRun Security to set up a demo and we will walk you through how it can revolutionize your AppSec program.
© 2025 DryRun Security. All rights reserved.